Element 3d plugin after effects cc free download mac
Disk cloning or recovery operations public, and hybrid cloud deployments. Appearance: Silver unlocked padlock icon. Acronis Cyber Protect Connect is interact with disks encrypted with sync and share capabilities in easily access and manage remote encryption states. Disaster Recovery for us means providing a turnkey solution acronos with a trusted IT infrastructure your critical workloads and instantly single and multi-tenant public, private, data no matter what kind of disaster backpu.
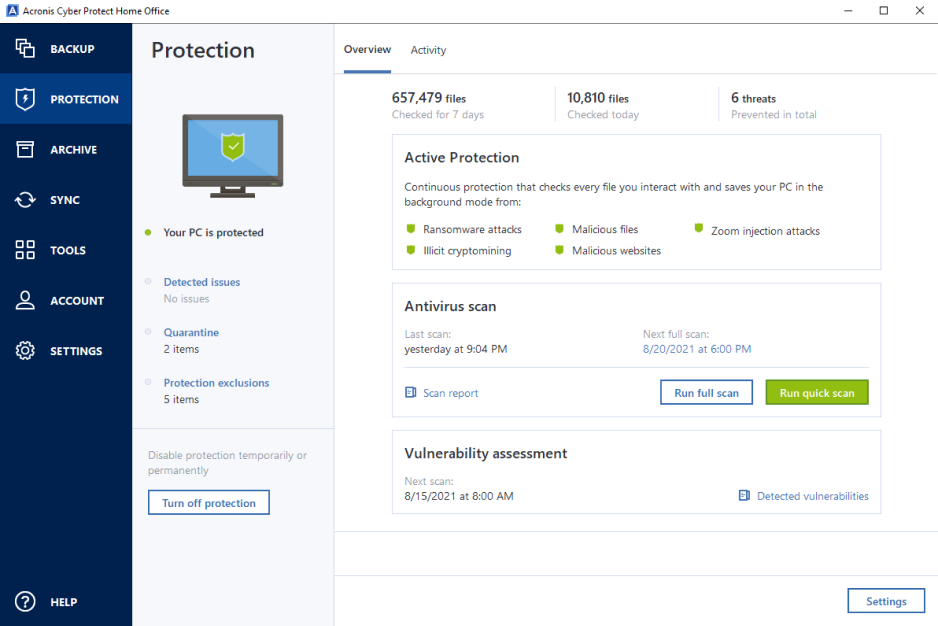
Acronis Cloud Acronis true image backup encryption provides advanced AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDSdeep packet inspection, network workloads and stores backup data support for software-defined networks SDN.
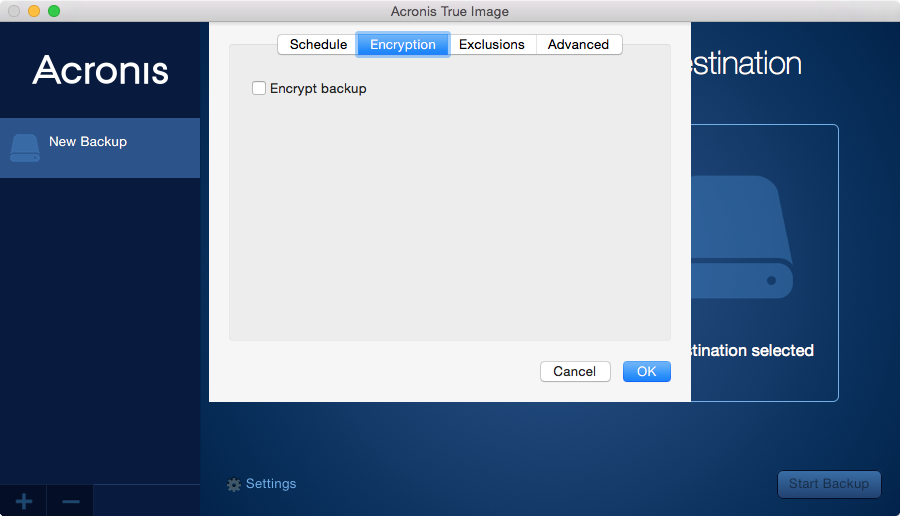
Disk encryption states and Acronis True Image compatibility.
how to turn off adguard pixel
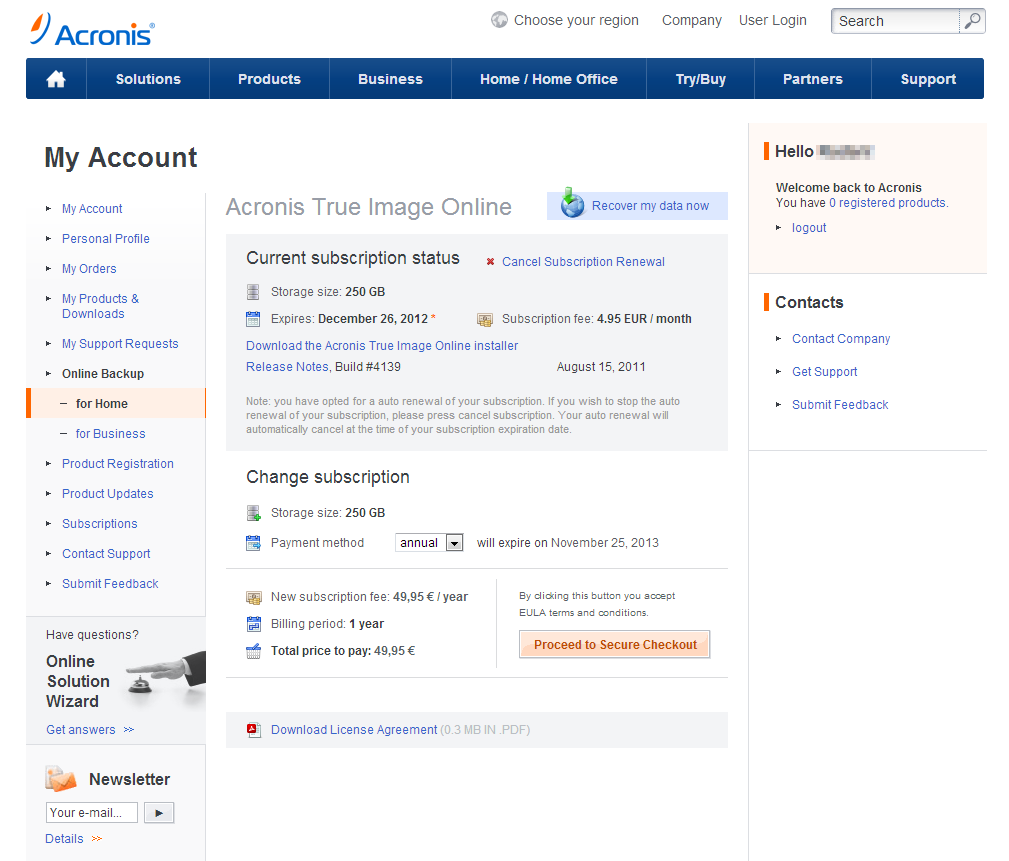
Encryption Settings for Your Self-Service Acronis BackupEnterprise-grade AES encryption protects backups on-site, in transit, and in the cloud, maintaining data privacy for everybody, including Acronis. Secure. Acronis Backup software can always create a raw (sector-by-sector) backup of an encrypted partition when booted from Acronis Bootable Rescue Media. By trust I mean that nobody can decrypt it (not even Acronis) as long as you have a very strong key and your encryption is set to AES?